Happy Holidays! It's always a busy time of year around home, but thankfully I got to take 10 days off work! I figured it was time to update the blog, with work related things.... wait a second I'm supposed to be relaxing! :)
Moving on.
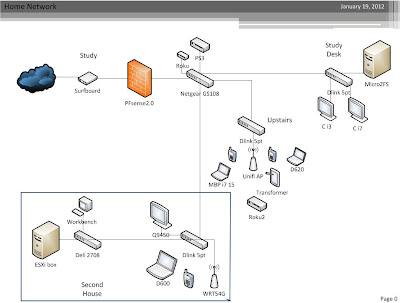
Since starting my new job nearly a year ago my home lab has been kept busy running several test environments for work. I watched my powerbill go up $30/m, despite using fairly power conservative hardware. Not to mention the $50/m second DSL line for firewall evals (nothing like the real world to proof something out.) Ok ok, maybe I could have skipped the 2nd internet connection, but still! At work, the warehouse data center has finally started to shape up. Our power work was just completed last month and everything seems to be running smoothly. No better time then now to colo a new lab box :).
Plus who wants this in their living room?
(Old home lab, testing HP switch gear and FreePBX phone system.)
Like 90% of everything else I build, I started by gathering recycled parts. After months a few months of cleaning and saving random bits from recycled systems before they headed to the e-waste bin, I finally came up with a random assortment of project leftovers, e-waste, and some "new" parts. The chassis was one I bought for a previous ESXi + OI all in one build that ended up shelved. The motherboard was a open box special off newegg, and the ASA/HP switch were left overs from a early switching lab. Now I realize to most people this is not what you would find headed for recycling and I would not let it. I try to keep a small stock of parts like this for in house use. You never know when you will need that 32GB of DDR3 or LSI HBA's.
System specs:
Supermicro SC826E1-R900 with hotswap powersupplies
(2) Intel Xeon x5650 2.66/12mg 6 core processors
Supermicro X8DT3-O with IPMI
(12) 16GB DDR3 ECC REG
(2) LSI 9211-8i HBA
(1) LSI 9211-8e HBA
(2) Intel 160gb x25
(5) Crucial M4 256gb
(5) Crucial M4 512gb
(2) HP 16GB Thumbnail flash drives for ESXi install
Storage:
Supermicro SC846A-R900B 24 bay JBOD
24x Seagate 1TB 7200rpm drives
Networking:
HP 1910-24G
Cisco ASA5505-SECPLUS
Backup:
Synology DS219j
2x3TB drives
I recently upgraded out licensing from vSphere Essentials to Essentials plus, but kept the old licensing for two test servers and this lab box. Once all setup, I should be able to VPN in and setup how ever many test boxes, maybe a game server or four, haha.
(Early picture with 48GB)
I can't wait to get this racked. Not only will it vastly increase the number of VM's I can run, but it will not longer cost me ~$80/m to run at home. I can not stress this enough- having a lab environment to test out routing issues, build server environments, and even built images in that is not directly associated with your production environment is critical! I got away with a Quad Core/32gb ram and a small HP n40l SAN for 15 machines, but it was painful.
Next up: Racking and storage configuration. I plan on building that ESXi + OpenIndiana + ZFS/NAPP-IT pass through All-In-One system and using it. Once everything is setup, it is time to play!








.JPG)